- True Positive: occurs when there is true attack, and reported properly. This IDS/IPS's AIM ;-)
- True Negative: occurs when did not report and alarm for legitimate network's activities.It is normal.
- False Positive: occurs when reported and alarmed for legitimate network's activities.this is A CUMBERSOME, need more searching to make sure it is attack or not. Unfortunately, most or all NIDS/NIPS are suffering form this drawback.
- False Negative: occurs when it failed to detect malicious network activity. This is A DISASTER!!!!
Now we need how to configure and adapt NIDS/NIPS's systems to avoid or eliminate the attacks. For example, to response against SYN Flood and UDP Flood, Snort product will be used here. Before applying that, let us see how can prevent SYN and UDP Floods:
- SYN Flood:
(1) Host A ------ SYN -----> Host B
(2) Host A <--- SYN,ACK ---- Host B
(3) Host A ----- ACK ----> Host B
Host A <- Conn. Estab -> Host B
What does a hacker do? Actually, he sends a lot of SYN (first step) and receive (SYN, ACK) packet. But he wall not send back ACK (step three) to server that causes the server or a victim to be waiting to answer all of these SYN packets that cause DOS/DDOS. Preventing of DOS/DDOS against TCP Handshake can be solved by one of two solutions:
- Terminate just the current connection: that allow next connection form same source. This can be done by send to RST flag to SYN (first step) to reset the connection. To implemet that add rst_snd, or rst_rcv, or rst_all depend on your case to Snort's rules.
- Block a acker for all time. This can be applied by installing Snort configured with inline feature.
Whereas UDP Flood is sending a lot of packets against a protocol's port that cause DOS/DDOS. Such of this flood can be prevented by sending based on the case one of the following packets:
icmp_net, icmp_host, icmp_port, and icmp_alllast packets report to a hacker the destination is not available that stop or terminate his connections caused DOS/DDOS.
The following part explains the installation and configuration's steps of Snort in order to meet DOS/DDOS's prevention:
First, be a root:
sudo -i
enter a password
Then, install the packages:
apt-get install build-essential libpcap0.8-dev libmysqlclient15-dev mysql-client-5.0 mysql-server-5.0 bison flex apache2 libapache2-mod-php5 php5-gd php5-mysql libphp-adodb php-pear libc6-dev g++ gcc pcregrep libpcre3-devNext, change to Snort's directory as setup it:
cd /home/mohd/Desktop/snort-2.8.4.1then type:
./configure --enable-dynamicplugin --with-mysql

If there is no error, type make (wait until this operation end) then type make install. At this point the installation is finished, now we need to adapt and configure Snort. Type in terminal (you are root) the following commands:


adduser snort
enter password
then type chsh :
chsh snortand change shell of /bin/true.
next, lock the account:
passwd snort -l
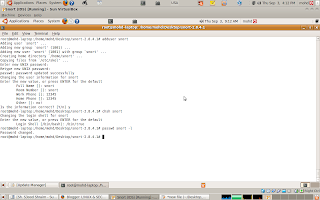
Now, make Snort' folders and configurations, type in trminal:
mkdir -p /etc/snort/rules /var/log/snortthen type each one individually:
chown -R root.snort /var/log/snort
chmod -R 770 /var/log/snort
cp etc/* /etc/snort/
cp rules/* /etc/snort/rules

Edit snort.conf file to make some of adaptations:
gedit /etc/snort/snort.conf &
search RULE_PATH line and replace it with:
var RULE_PATH /etc/snort/rules

At this point, snort's installation is finished, now we need to check it. Type in terminal (the output should be appear like the picture):
snort -v
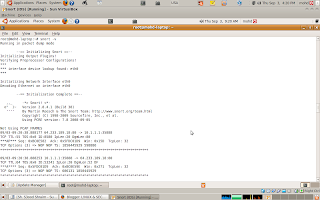
If everything is OK, now we need to configure database and ACID web site to simplify the reading of attacks. Following part depicts that:
change to /var/www directory
ch /var/wwwdownload the base package:
wget http://easynews.dl.sourceforge.net/sourceforge/secureideas/base-1.3.9.tar.gz
tar xvfz base-1.3.9.tar.gz

then allow apache web server to read it's files:
chown -R www-data.www-data base
Install a few Pear modules:
pear install Image_Color Image_Canvas-alpha Image_Graph-alpha

next, open Firefox browser to install (setup) base's web application:
in Firefox type http://localhost/base will present 5 screens. Press continue to start.
First screen: Enter the path to ADODB that is /usr/share/php/adodb

Second screen: enter data base information as it appear it the picture

Third screen: enter admin username/password
Fourth screen: press Create BASE AG button.

Fifth screen: done, now press step 5 link (in the bottom)

at this point, BASE's web application is configured ;-)
Now, we need to configure data base to log snort's packets into data base and use it by previous bast web application; as following:
Login in MySQL data base as a root:
mysql -u root -p
enter a password
then, type:
mysql> create database snort;
mysql> grant all privileges on snort.* to 'snort'@'localhost' identified by 'password';
mysql> exit

then, export data base schemas:
mysql -D snort -u snort -p < /home/mohd/Desktop/snort-2.8.4.1/schemas/create_mysql enter snort's password (that is password).

Edit snort.conf asgain to configure a data base as it appear it the picture;
gedit /etc/snort/snort.conf &

Until here we finished all of the configurations Time now for testing:
to run Snort as a detection system; open new terminal ant type:
snort -v -c /etc/snort/snort.conf -l /var/log/snort/ -i eth0

after that, open the Firefox browser, and type http://localhot/base

and monitor attacks against you ;-)
this post explained Snort as IDS. Next one -inShaAllah- will explain Snort's configuration to be IPS.
the end.






